Beyond Passwords: Identity Management for Secured Authetication
In today's digital landscape, logging into a website isn't just about clicking "remember me." It's a complex process of identity management and authentication, ensuring the online experience is secure and seamless.
This blog post discovers the inner workings of this fascinating process, explores familiar concepts like cookies and sessions, along with modern solutions like tokens and JSON Web Tokens (JWTs). It will unveil the advantages of Single Sign-On (SSO) and discover how OAuth 2.0 allows secure data sharing without passwords. It will also highlights innovative solutions like QR code-based login, offering a glimpse into the future of authentication.
By the end, you'll have a deeper understanding of these methods and how they help to secure online communication.
Identity Management using Sessions
A session is a temporary interaction between a web server and a user's web browser. It begins when a user accesses a website and ends when the user closes the browser or remains inactive for a specified period (session timeout). During a session, the server can store and retrieve information associated with the user, such as authentication credentials, preferences, and session data.
When a user logs in to a website, their identity needs to be verified to grant
access to restricted resources. Session-based login identity management involves the following steps:
Authentication: The user provides their credentials (e.g., username and password) through a login form. The server validates these credentials against stored user data (e.g., in a database).
Session Initialization: Upon successful authentication, the server creates a unique session identifier (session ID) and associates it with the authenticated user's identity. This session ID is typically stored as a cookie in the user's browser.
Session Tracking: As the user navigates through the website, the session ID is included with each request, allowing the server to recognize and associate subsequent requests with the correct session.
Access Control: The server verifies the session ID and checks whether the associated session is authenticated and authorized to access the requested resources. If the session is valid, the user is granted access; otherwise, they may be redirected to the login page.
Session Termination: When the user logs out or the session expires (due to inactivity or reaching the session timeout), the server destroys the session and invalidates the session ID, removing access to restricted resources.
Implementation Considerations
Session Storage: Sessions can be stored either on the server-side or client-side (in cookies). Server-side storage is more secure and scalable, while client-side storage may be used for lightweight sessions or to offload server resources.
Session Security: Protecting session data is paramount to prevent unauthorized access and session hijacking. Techniques such as encrypting session data, using secure cookies (with the Secure and HttpOnly attributes), and implementing measures to detect and prevent session fixation and session replay attacks are essential.
Session Management Frameworks: Many web development frameworks provide built-in support for session management, offering features such as session persistence, expiration handling, and security enhancements.
Identity Management using Tokens
Use of tokens has emerged as a powerful and versatile solution for handling authentication and authorization securely. Tokens are strings of characters that serve as proof of authentication or authorization. They are generated by the server and are provided to the client upon successful authentication.
Tokens can be broadly categorized into two types:
Authentication Tokens: These tokens are used to verify the identity of a user during the login process. Once a user logs in successfully, an authentication token is generated and provided to the client. This token is then included in subsequent requests to the server to authenticate the user's identity.
Authorization Tokens: Authorization tokens, also known as access tokens, are used to grant access to protected resources on the server. These tokens are obtained after successful authentication and are used to authorize specific actions or access levels on the website.
User Authentication: When a user attempts to log in to a website, they provide their credentials (such as username and password). The server verifies these credentials and, if valid, generates an authentication token.
Token Generation: Upon successful authentication, the server generates a unique authentication token and associates it with the user's session. This token is then sent to the client (usually in the form of a JSON Web Token or JWT) and stored securely.
Token Storage: The client stores the authentication token securely, typically in local storage or a browser cookie. This token serves as proof of the user's identity and is included in subsequent requests to the server.
Token Verification: When the client makes a request to access protected resources or perform authorized actions on the website, it includes the authentication token in the request headers. The server verifies the token to ensure that the request is coming from an authenticated user.
Token Expiry and Renewal: Authentication tokens often have an expiration time to enhance security. When a token expires, the client must obtain a new token by re-authenticating with the server. This helps mitigate the risk of token theft or unauthorized access.
JWT – JSON Web Tokens:
Tokens can be of various types, including JSON Web Tokens (JWT). JWTs are self-contained units built on a standard format (RFC 7519). They encapsulate three parts: header, payload, and signature. The header and payload carry information about the token, such as its type, expiration time, and user claims (e.g., username, roles). The signature, created with a secret key or public/private key pair, ensures the token's authenticity and integrity.
The self-contained nature of JWTs enables their validation without server-side communication. The signature can be verified using the public key, and claims can be decrypted if encrypted. This offers enhanced security as sensitive information isn't transmitted in plain text.
JWTs can be configured with expiration times, ensuring they don't become perpetual after issuance. They can also include custom claims, providing flexibility for specific use cases.
Benefits
Stateless Authentication: Unlike session-based authentication, which requires the server to maintain session state, token-based authentication is stateless. This makes it easier to scale and maintain server infrastructure.
Enhanced Security: Tokens can be digitally signed and encrypted to prevent tampering and unauthorized access. Additionally, the use of short-lived tokens reduces the risk of session hijacking.
Cross-Domain Authentication: Tokens can be used to implement single sign-on (SSO) and enable users to authenticate across multiple domains or applications seamlessly.
Granular Access Control: Authorization tokens allow for fine-grained access control, enabling websites to enforce access policies based on user roles and permissions.
Identity Management using SSO
Single Sign-On (SSO) is an authentication process that allows users to access multiple applications or websites with a single set of login credentials. Instead of requiring users to remember and enter different usernames and passwords for each service they use, SSO enables them to authenticate once and gain access to all authorized resources seamlessly.
The SSO process typically involves three main components:
Identity Provider (IdP): The Identity Provider (like Google Sign-in, Azure Active Directory, Okta, Auth0 and OneLogin) is responsible for authenticating users and providing identity information to service providers. It verifies the user's identity using various authentication methods, such as passwords, biometrics, or multi-factor authentication (MFA).
Service Provider (SP): The Service Provider relies on the Identity Provider for user authentication. Once the user is authenticated by the IdP, the SP grants access to its resources without requiring additional login credentials.
User: The end-user initiates the authentication process by accessing a service provided by the SP. Upon authentication, the user's identity is verified by the IdP, and access is granted to the requested service.
Benefits
Enhanced User Experience: SSO simplifies the login process for users, eliminating the need to remember multiple sets of credentials. This leads to a more convenient and user-friendly experience.
Improved Security: With SSO, user authentication is centralized and managed by the Identity Provider, which often implements robust security measures such as MFA and encryption. This helps mitigate the risk of unauthorized access and data breaches.
Increased Productivity: By reducing the time and effort spent on managing multiple login credentials, SSO enables users to access resources more quickly, leading to improved productivity and efficiency.
Simplified Administration: Website administrators benefit from simplified user management and authentication processes. Instead of managing user accounts across multiple systems, they can centralize user authentication and access control through the Identity Provider.
Scalability: SSO facilitates seamless integration with new applications and services, making it easier to scale authentication capabilities as the organization grows.
Identity Management using OAuth2
OAuth 2.0 is an authorization framework that enables third-party applications to access resources on behalf of a user without requiring the user's credentials to be shared directly. It provides a standardized way for users to grant access to their resources hosted on one website to another website, without divulging their credentials (such as username and password).
Key Components of OAuth2
Resource Owner: The resource owner is the user who owns the data or resources being accessed. In the context of website login identity management, the resource owner is the user whose identity is being authenticated.
Client: The client is the application requesting access to the user's resources. This could be a web application, mobile app, or any other software component.
Authorization Server: The authorization server is responsible for authenticating the user and obtaining their consent to grant access to the client application.
Resource Server: The resource server hosts the protected resources that the client application wants to access on behalf of the user. Client Credentials (to verify the client's identity and legitimacy) and User information (details about the user associated with the access token) are stored by resource server.
OAuth2 – The Working Process
User Initiation: When a user attempts to log in to a website using OAuth 2.0, the website redirects the user to an authorization server (e.g., Google, Facebook) to authenticate their identity.
Authorization Request: The website sends an authorization request to the authorization server, specifying the requested permissions and scope of access.
User Consent: The authorization server prompts the user to grant or deny access to their resources.
Authorization Grant: If the user grants access, the authorization server issues an authorization grant (e.g., access token) to the website.
Token Exchange: The website exchanges the authorization grant for an access token that can be used to access the user's resources.
Access Resources: The website can now access the user's resources (e.g., profile information, email address) using the access token obtained from the authorization server. (Things that were embedded with the access token are Identifier, Subject, Issuer, Audience, Scope and Expiration)
Token Expiry and Refresh: Access tokens have a limited lifespan. When an access token expires, the website can use a refresh token to obtain a new access token without requiring the user to log in again.
Benefits
Improved Security: OAuth 2.0 reduces the risk of credential theft and unauthorized access by allowing websites to access resources without storing or transmitting user credentials.
User Convenience: Users can log in to websites using their existing accounts from popular identity providers, eliminating the need to create new accounts or remember additional passwords.
Scalability and Interoperability: OAuth 2.0 is widely adopted and supported by major technology companies, making it scalable and interoperable across different platforms and services.
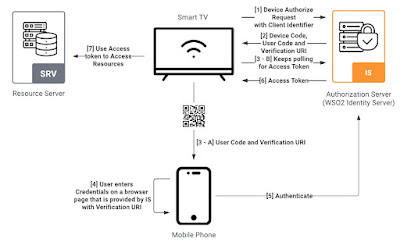
Identity Management using QR Code Login
QR code login is a method of authentication that utilizes Quick Response (QR) codes to verify a user's identity. Instead of typing in a username and password, users simply scan a QR code displayed on the website's login page using their smartphone or other QR code scanning device. This process streamlines the login experience, eliminating the need for users to remember complex passwords.
QR Code – Login Process
Generating QR Code: When a user navigates to the login page of a website that supports QR code login, the server generates a unique QR code associated with the user's account.
Scanning QR Code: The user scans the QR code using a compatible device (e.g., smartphone). This action triggers the device to send a secure authentication request to the server.
Authentication Verification: The server receives the authentication request and validates the QR code along with the associated user account. If the QR code is valid and matches the user's account, the login is approved, and the user gains access to the website.
Benefits
Enhanced Security: QR code login eliminates the need for passwords, reducing the risk of unauthorized access due to password theft or interception. Additionally, each QR code is unique and time-sensitive, further enhancing security.
Convenience: QR code login provides a seamless and user-friendly authentication experience. Users can quickly scan the QR code without the hassle of typing passwords, making the login process more efficient.
Multi-factor Authentication (MFA): QR code login can be combined with other authentication factors such as biometrics or one-time passwords (OTP), adding an extra layer of security to the login process.
Reduced Password Fatigue: With QR code login, users no longer need to remember complex passwords or worry about password management. This reduces the likelihood of password-related issues such as forgotten passwords or password resets.
A Quick Comparison:
Conclusion
It is essential to recognize that there isn't a one-size-fits-all approach to identity management. Depending on the use case and the level of security demanded, organizations may implement one or more, or even a combination of many of these authentication methods. Whether it's the simplicity of QR code-based login, the robustness of token-based authentication, the convenience of Single Sign-On (SSO), or the versatility of OAuth 2.0, each method serves a unique purpose in safeguarding identities and securing online interactions.
As technology continues to evolve and new threats emerge, the landscape of identity management will undoubtedly continue to evolve as well. By embracing a holistic approach that leverages the strengths of various authentication methods, organizations can adapt to the ever-changing security challenges of the digital world. Ultimately, the goal remains the same: to ensure that users can access their digital resources securely, seamlessly, and with confidence, no matter where they are or what device they're using.
Cheers,
Venkat Alagarsamy








Comments
Post a Comment